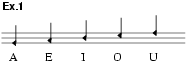
Cryptography (‘secret writing’) includes any method of masking a message. Sometimes the act of communication is itself concealed, for example by the use of invisible ink. More commonly, an overt message is disguised by code or cipher. In code an arbitrary assemblage of letters or numbers is assigned some specific meaning, or an ordinary word or phrase may be allotted some quite different significance. In cipher, the letters of a message are systematically transformed, either by changing their order or by replacing them with other letters or symbols. Both code and cipher principles can facilitate communications as well as conceal them, as for example in the Morse code (strictly a cipher) and in the invention of artificial languages. All these procedures are akin to some aspects of music. Thus ‘key’ is a basic common concept, while pitch and rhythm have evident semantic application. Indeed, music has often been conceived and described as a communication intelligible only to the initiated, which is precisely what language-structures in general and cryptograms in particular are designed to be.
Many cryptologists have been notable musicians. Among composers, Tartini, Michael Haydn, Schumann and Elgar are known to have been interested in cryptography. There is some evidence (e.g. Kahn, 1967, p.563) that the two abilities are positively correlated. The connection was also recognised and used in World War II by the British crypto-analytic service, candidates for which were asked among other things whether they could read an orchestral score. It is not surprising, then, that musical symbols or ideas should have been used in cryptography and allied disciplines from the earliest times, nor that quasi-cryptographic ideas should have been freely used in music. This article considers those separate areas in turn, dealing with each in chronological order, and then in conclusion discusses their occasional overlap.
1. Cryptography using musical ideas and symbols.
2. Other communication systems using musical symbols.
3. Music using cryptographic and related concepts.
ERIC SAMS/R
The most obvious method, the assignment of letters to individual notes of music, seems to have been the earliest and has certainly remained the commonest. The late 15th-century manuscript Rules for Carrying on a Secret Correspondence by Cipher (GB-Lbl Sloane 351, f.15b) describes a musical cipher. Symbols for 24 letters and the word ‘et’ are formed by using five different pitches on a three-line staff and altering the stem directions and note values. The five vowels are represented as in ex.1. As an illustration, the scribe has spelt out in his music-cipher the words ‘In nomine summe et individue trinitatis hoc opus incipio’. The earliest documented system thereafter seems to be the analogous cipher used about 1560 by Philip II of Spain. This begins as in ex.2 and continues similarly with different note values. By the end of the 16th century some very complex systems were in practical use. Thus the papal cryptographic service about 1596 used a music-cipher of nine different pitches each variable in eight ways, yielding a possible 72 symbols. Such proliferation is over-elaborate, and the simpler 11 × 2 system published by Giovanni Porta (c1600, in later editions of his seminal work on cryptography) found more general favour (ex.3).
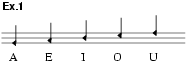
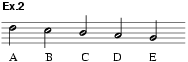
Many other possible uses of musical symbols were exploited by cryptographers. In 1596 Porta described a method of communication whereby a beleaguered city could send messages by ringing bells in a prearranged permutation, for example one bell once = A, twice = B, thrice = C; a second bell once = D; and so on. By 1650 Athanasius Kircher had transferred this idea to the orchestra, by allotting up to four successive notes among six instruments; thus one note from the first instrument would mean the letter A, two notes B, and so on. In 1685 Friderici proposed a number of novel and ingenious music-ciphers (such as ex.4). Nor were the visual aspects of music neglected; thus a 17th-century manuscript (Lbl Add.45850M) when folded spells out a message, supposedly to Charles II, with the stems and tails of notes.

In general the cryptographic textbooks and source-books continued to describe some form of Porta’s basic table (ex.3), which recurs in readily recognizable adaptations throughout the 16th and 17th centuries (Davies, 1967). Between 1620 and 1685 it appeared in five major works published in England, Germany and Italy (Schwenter, Godwin, Kircher, Schott, Friderici). Telemann may well have been referring to it when he wrote in the oratorio Der Tag des Gerichts of having been offered instruction in a secret method of ‘discovering by means of music the dealings of ambassadors and generals, and conveying orders to them’.
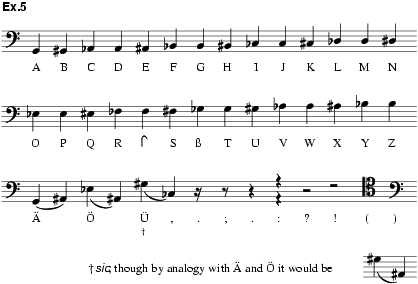
The Porta system evolved with music history. A specimen in the Foreign Office archives from about 1750 uses crotchets and quavers with treble and bass clefs (Schooling, 1896). Another, suggested by Philip Thicknesse in 1772, uses crotchets and minims with treble clef and key signature for extra authenticity. In the late 18th and early 19th centuries the system appears in textbooks by Guyot in France, Hooper in England and Klüber in Germany, in the form of a cipher-wheel on which the notes and corresponding letters are written round in two circles, one fixed and one movable. This device, of vital importance in the history of general cryptography (cf Kahn, 1967, pp.128–9) permits frequent resetting, thus baffling the hostile analyst. In these sources also the cipher further evolves, in the same interest, towards the random allocation of cipher letters to musical notes, the occasional representation of one letter by a two-note group, and in general a policy of analogy with real music, at least in appearance (for which purpose Klüber recommended the addition of sharps and flats). This had always seemed desirable for cryptographic reasons. Thus the papal encipherers had added to their music-cipher messages an ostensibly relevant liturgical text, so as to avert suspicion. In the later 18th and early 19th centuries the possibility of combining real cipher with real music was the subject of lively experiment and debate (‘Cipher’, Rees’s Cyclopaedia, 1819–20). A notable contribution was made by Michael Haydn who (according to his biographers, 1808) invented an elaborate music-cipher of his own (ex.5) presumably for communication purposes but perhaps for composition as well. At least it strikingly foreshadows cipher systems later used as compositional devices (see ex.10 below); and it may even have been designed (e.g. in its treatment of modified vowels) to yield results which were not too unlike real music. But it remained a private initiative. The only documented contemporary use of music-cipher in practice, in the French diplomatic service (correspondence between the Duke of Havre and the Duke of Lorges, GB-Lbl Add.32259, f.180v), relies on a Porta-type system which is neither convincing musically nor secure cryptographically. This use continued as late as 1800. Nor was the type entirely extinct in the 20th century; the first solved intercept of the New York City Police Department (‘Codes are Fragile’, 1952) was a series of melodic lines in the treble clef which turned out to be a note-for-figure encipherment of illegal wagers – furnished with occasional accents and pauses in an optimistic attempt at verisimilitude.
Meanwhile, on a different (not strictly cryptographic) level, musical sounds or symbols had been considered as the basis for more general semantic systems and structures. One pioneer was Bishop Wilkins, who suggested (1641) that the ordinary notes of a musical instrument might be used to express not only letters and words but things and notions, so that ‘there might be such a general language as should be equally speakable by all nations and peoples’. Leibniz (c1678) put forward a similar suggestion for an artificial language consisting solely of tones and intervals (Couturat, 1903). There must also have been practical research and experiment in this area, for in 1800 (as Klüber recorded, 1809) pupils at a school for the blind in Paris were ‘reading’ phrases played on the violin. The (unspecified) techniques used may have been a Porta-type system extended for communication purposes (as by Bertini, 1811). But they were more likely to have been precursors of the ideas later developed by Jean-François Sudre (1787–1862), whose pupils could also converse with him via the violin. By 1817 he had constructed a complete artificial language, in which any seven different symbols could be combined five at a time, with variations of order and stress. The seven sol-fa syllables or pitches formed one obvious basis of his system, which incorporated such quasi-musical ideas as the use of ‘domisol’ (i.e. the perfect triad) to mean ‘God’ and its retrograde form to mean ‘Satan’. Similarly ‘sollasi’ means ‘ascend’ and ‘silasol’ ‘descend’. The idea was officially welcomed in its day as having potential practical value; but it found no lasting application, and was in effect superseded by the invention of the Morse code. With the demise of Sudre’s system the last serious attempt to exploit purely musical resources for purely linguistic purposes came to an end.
No doubt the idea of using the elements of music to convey extra-musical semantic significance (whether audible or inaudible, overt or covert) is as old as music itself. Some devices depend on written notation. Words can be sung, for added emphasis, to their corresponding solmization names (e.g. ‘re’ for ‘king’, ‘sol’ for ‘sun’). Examples are found from Josquin to Schütz (Wessely, 1973; see also Solmization). Eye music, adding visual meaning to written scores, is found as late as Bach, some of whose music may also contain the idea of a ritual symbolism of gesture, motion or number (Krause, 1964). Numbers can be signified by intervals or instruments, voices or entries, from the 14th century (Wessely, 1973) to Bach (Krause, 1964; Geiringer, 1956). The numbers thus conveyed may then be used according to strict cryptographic principles to encipher letters of the alphabet, according to the system already described above. This device was used in the early 18th century by J.C. Faber, whose Neu-erfundene obligate Composition (MS, D-W) enciphers the name ‘Ludovicus’ by the number of notes allotted to the solo trumpet in each of the nine movements. Using the Latin milesian alphabet (A=1, B=2, C=3 to I=9, K=10 to S=90, T=100 to Z=500), which Faber stated was taken from Tabourot (1584), the solo trumpet plays 20 notes in the first movement, at the head of which is written ‘L=20’, 200 notes in the second, at the head of which is written ‘U=200’ and so on (see also Numbers and music). The same determined encipherer also used a Porta system analogous to ex.3 as a means of incorporating messages, for instance in the viola part of a quartet.
The
most common of all such devices however was the use of the letter-names of
notes to create themes from words or (more usually) names of people. This idea
too no doubt dates back to the beginning of letter nomenclature. It is
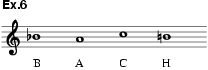
particularly associated with the name of Bach, which in German usage can be
written as in ex.6. Bach himself and his contemporaries
incorporated that phrase in many works (as did Beethoven, Schumann, Liszt,
Rimsky-Korsakov, Busoni and several others; see B–a–c–h). Bach showed further
ingenuity in his seven-part canon over a ground of F–A–B–E, headed
‘FABERepetatur’ – possibly a suitably cryptic allusion to J.C. Faber himself or
a kinsman. Such ideas flourished especially in the common ground between music
and literature that was increasingly cultivated in the 18th and 19th centuries;
they are, for example, typical of Jean Paul and occur in his novel Flegeljahre
(1804–5). As a consequence, more letters and ideas were found musical
equivalents than the standard A to G (and H, the German B![]() ). For example, ‘S’ can be considered as
the equivalent of the note E
). For example, ‘S’ can be considered as
the equivalent of the note E![]() , because the German name of the latter is ‘Es’; this
enabled Friedrich Fesca to begin a string quartet with F–E–E
, because the German name of the latter is ‘Es’; this
enabled Friedrich Fesca to begin a string quartet with F–E–E![]() –C–A, literally his own signature
tune. It helped Spohr sportively to render his own name as in ex.7 (po stands for portamento; the old-style
crotchet rest looks like ‘r’). At one extreme, ideas of this kind could be used
in grave commemoration of the death of Schubert, as in the fugues written on
the musical letters of his name by Stadler and Sechter; at the other, they
could inspire such jeux d’esprit as John Field’s tribute to his hostess
Mme Cramer (MS, 1832) in the form of two grateful melodies on B–E–E–F and
C–A–B–B–A–G–E.
–C–A, literally his own signature
tune. It helped Spohr sportively to render his own name as in ex.7 (po stands for portamento; the old-style
crotchet rest looks like ‘r’). At one extreme, ideas of this kind could be used
in grave commemoration of the death of Schubert, as in the fugues written on
the musical letters of his name by Stadler and Sechter; at the other, they
could inspire such jeux d’esprit as John Field’s tribute to his hostess
Mme Cramer (MS, 1832) in the form of two grateful melodies on B–E–E–F and
C–A–B–B–A–G–E.

The
greatest and most prolific exponent of such notions, whether serious or genial,
was Schumann. The musical letters of his own name, S–C–H–A, form a main theme
of Carnaval, where they are also found as A–S–C–H, the name of his
friend Ernestine von Fricken’s home town, and anagrammatized as A–S–H–C. The
A–S component is enciphered variously as two notes (A, E![]() ) or as one (As = A
) or as one (As = A![]() in German). Schumann also used, in
published music, A–B–E–G–G and G–A–D–E (names of friends); F–A–E (standing for
‘frei aber einsam’, free but lonely, a device also used in music by Joachim);
and H (the answer to a riddle on the letter H). His other overt music–ciphers
used in extant letters or manuscripts include A–C–H, A–D–E, B–E–D–A (a pet name
for Clara Wieck), B–E–S–E–D–H (the nearest equivalent to the name of a friend,
Bezeth), E–H–E (‘marriage’) and, no doubt the longest example on record,
(L)–A–S–S D–A–S F–A–D–E, F–A–S–S D–A–S A–E–C–H–D(T)–E, or ‘leave what is trite,
hold fast to the right’, in a musical rebus.
in German). Schumann also used, in
published music, A–B–E–G–G and G–A–D–E (names of friends); F–A–E (standing for
‘frei aber einsam’, free but lonely, a device also used in music by Joachim);
and H (the answer to a riddle on the letter H). His other overt music–ciphers
used in extant letters or manuscripts include A–C–H, A–D–E, B–E–D–A (a pet name
for Clara Wieck), B–E–S–E–D–H (the nearest equivalent to the name of a friend,
Bezeth), E–H–E (‘marriage’) and, no doubt the longest example on record,
(L)–A–S–S D–A–S F–A–D–E, F–A–S–S D–A–S A–E–C–H–D(T)–E, or ‘leave what is trite,
hold fast to the right’, in a musical rebus.
It
has been suggested that Schumann used a three-line, eight-note cipher (on a
system derived from Klüber, 1809, with whose work he has been shown to be
familiar; see Sams, ‘A Schumann Primer’, 1970) much as in ex.9 below,
especially for the purpose of making themes with the covert significance of
‘Clara’ (Schumann, née Wieck); and that Brahms also used such themes with the same
meaning (Sams, 1971 and forthcoming). Brahms was also much given to the
meaningful use of musical letters. He seems to have used his own, B–A–H–S, in
his A![]() minor organ
fugue. He modified the F–A–E idea to F–A–F, standing for ‘frei aber froh’, free
but happy, which was used in many works from the Serenade no.1 to Symphony
no.3. The notes A–G–A–(T)–H–E, A–D–E are used as a valediction to Agathe von
Siebold in the Sextet op.36 and arguably in other works (Sams, ‘Brahms and his
Musical Love-Letters’, 1971). In correspondence Brahms referred to Adele
Strauss as the notes A–E
minor organ
fugue. He modified the F–A–E idea to F–A–F, standing for ‘frei aber froh’, free
but happy, which was used in many works from the Serenade no.1 to Symphony
no.3. The notes A–G–A–(T)–H–E, A–D–E are used as a valediction to Agathe von
Siebold in the Sextet op.36 and arguably in other works (Sams, ‘Brahms and his
Musical Love-Letters’, 1971). In correspondence Brahms referred to Adele
Strauss as the notes A–E![]() (A.S.) and to Gisela von Arnim as the notes G
(A.S.) and to Gisela von Arnim as the notes G![]() –E–A (Gis-e-la). This ingenious combination of German
note-names with solmization names, the typical French usage, recurs in the use
of B
–E–A (Gis-e-la). This ingenious combination of German
note-names with solmization names, the typical French usage, recurs in the use
of B![]() –A–F (B-la-F) in a
string quartet written for Belyayev by Borodin, Glazunov, Lyadov and
Rimsky-Korsakov. It has been suggested that Tchaikovsky made analogous use of a
friend’s name, D–E(s)–Si–re–E (Brown, 1978). Glazunov composed on the theme of
his own pet name, S–A–C–H–A; César Cui linked the musical letters B–A–B–E–G in
his wife’s maiden name (Bamberg) with his own initials, C–C. Smetana not only
composed with his own monogram B–S and the musical letters F–E–D–A in the name
Froejeda, but also enciphered the year 1862 as the first, eighth, sixth and
second degrees of the scale.
–A–F (B-la-F) in a
string quartet written for Belyayev by Borodin, Glazunov, Lyadov and
Rimsky-Korsakov. It has been suggested that Tchaikovsky made analogous use of a
friend’s name, D–E(s)–Si–re–E (Brown, 1978). Glazunov composed on the theme of
his own pet name, S–A–C–H–A; César Cui linked the musical letters B–A–B–E–G in
his wife’s maiden name (Bamberg) with his own initials, C–C. Smetana not only
composed with his own monogram B–S and the musical letters F–E–D–A in the name
Froejeda, but also enciphered the year 1862 as the first, eighth, sixth and
second degrees of the scale.
In England, Elgar was a skilled cryptologist. He successfully solved a well-known challenge cipher, to which eminent experts later thought it worthwhile to publish their own solutions; he constructed a difficult if not impossible cryptogram; he made cipher entries in diaries and notebooks. One of his earliest works was an Allegretto for violin and piano on G–E–D–G–E, the name of a friend. It seems reasonable on the facts to conjecture that he used private ciphers in some of his compositions, and that suggestion has often been made in respect of the ‘Enigma’ Variations. The theme of Granville Bantock’s Helena Variations is fashioned from his wife’s initials, H–F–B.
The
first major composer to make serious and acknowledged use of a detailed and
coherent cipher system was Ravel, who in 1909 used ex.8 (except that, presumably to avoid repetition, H was given
its German equivalent, B![]() ) to encipher the name Haydn in a commemorative
Menuet for piano. Similar pieces were written on the same system at the same
time by Debussy, Dukas, Hahn and d’Indy. The same 7 × 4 system was used again
in 1922 by Ravel and others (Schmitt, Enescu, Aubert, Koechlin, Ladmirault and
Roger-Ducasse) in tribute to Fauré. The idea seems to have appealed to Ravel
who (alone, apart from Schmitt) elected to encipher the whole name of Gabriel
Fauré. In 1929 another group of composers (Poulenc, Honegger, Milhaud, Ibert
and others) used cipher in celebration of Albert Roussel; this time no uniform
system was adopted. Some are unspecified, Poulenc’s for example; but it can be
inferred from the score of his Pièce brève sur le nom d’Albert Roussel
to be an 8 × 3 arrangement as in ex.9. The name ‘Albert’ is also
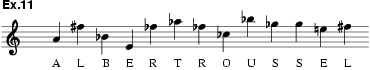
enciphered backwards to make an additional theme. Of especial interest is Honegger’s
encipherment system, ex.10, which is worth comparing
with Michael Haydn’s (ex.5). Honegger’s actual
compositional procedure is shown in exx.11 and 12.
) to encipher the name Haydn in a commemorative
Menuet for piano. Similar pieces were written on the same system at the same
time by Debussy, Dukas, Hahn and d’Indy. The same 7 × 4 system was used again
in 1922 by Ravel and others (Schmitt, Enescu, Aubert, Koechlin, Ladmirault and
Roger-Ducasse) in tribute to Fauré. The idea seems to have appealed to Ravel
who (alone, apart from Schmitt) elected to encipher the whole name of Gabriel
Fauré. In 1929 another group of composers (Poulenc, Honegger, Milhaud, Ibert
and others) used cipher in celebration of Albert Roussel; this time no uniform
system was adopted. Some are unspecified, Poulenc’s for example; but it can be
inferred from the score of his Pièce brève sur le nom d’Albert Roussel
to be an 8 × 3 arrangement as in ex.9. The name ‘Albert’ is also
enciphered backwards to make an additional theme. Of especial interest is Honegger’s
encipherment system, ex.10, which is worth comparing
with Michael Haydn’s (ex.5). Honegger’s actual
compositional procedure is shown in exx.11 and 12.




The simpler model of ex.8 was used by Arnold Bax in his Variations on the Name Gabriel Fauré in 1949. Otherwise outside France the German letter-name tradition continued in the 20th century as in the 19th. In Berg’s Chamber Concerto the musical letters in the names Schoenberg, Webern and Berg (S–C–H–B–E–G, E–B–E, B–E–G) are incorporated in the music as personal symbols. Thea Musgrave made a similar use of the names of the first Viennese school in her Chamber Concerto no.3. Dmitry Shostakovich, in his Eighth String Quartet and elsewhere, used his monogram D–S–C–H as a theme, which Ronald Stevenson also used, in homage, in his Passacaglia; while Everett Helm has signed more than one composition with the musical initials E–H. In Bussotti’s contemporary theatre-piece La passion selon Sade, D–Es–A–D–E is interlocked with B–A–C–H. But the most striking developments of the 1960s came from what might be called the French tradition, in the form of Olivier Messiaen’s ‘communicable language’ (ex.13) and complementary leitmotifs (ex.14) which together make the complete cipher and code system used in the organ work Méditations sur le mystère de la Sainte Trinité (Halbreich, 1972). Ex.13 is used to encipher extended quotations (in French) from the Summa theologica of St Thomas Aquinas; ex.14 and other leitmotifs symbolize spiritual entities or basic concepts such as ‘to be’ or ‘to have’.


It seems entirely fitting that such a system should have evolved in the only milieu ever to have produced real music on themes overtly derived from cipher, and the only milieu ever to have produced a complete artificial language with musical elements. There is an evident affinity between ex.13 and ex.10 (most clearly in the first eight notes of each). Although the ‘theme of God’ means the same in its retrograde form, unlike François Sudre’s ‘domisol’, the relation between his ‘language’ and Messiaen’s is also manifest, especially when we learn that the latter’s ascending ‘to be’ is counterbalanced by the descending theme ‘to have’.
The two streams of music and cryptography, usually quite separate, sometimes converge. That trend became more marked in the later years of the 20th century. The combinative impetus came from both sides. Cryptographers have always striven to make their music-ciphers as much like real music as possible in order to enhance their effectiveness as cipher. Some composers, conversely, may well have felt that their music was enriched by a judicious admixture of cryptographic elements. The use of cipher themes seems to have begun with J.C. Faber and may well have continued with Michael Haydn, Schumann and Elgar. The undisguised use resumed in France with Ravel, Poulenc, Honegger and others, and culminated in Messiaen. But, as Norman Cazden showed in 1961, modern scores present unrivalled opportunities for encipherments of all kinds, and no doubt there are undeclared exponents of undisclosed cipher techniques of musical composition.
Critical mention of this practice tends to be uncomprehending and deprecatory. But on the evidence it derives from a true intuition that music and semantics have deep roots in common ground. Nor is this intuition confined to musicians; Thomas Mann for example in Dr Faustus envisaged a 12-note system which could also be used as cipher, suffusing the music with new quasi-verbal meaning. It is perhaps significant that in the past all the best-known and most frequent examples have been encipherments of names – presumably because names, of all words, are the least fixed and most fluid in meaning, and therefore the most closely akin to musical motifs as generally understood. With changing techniques and attitudes cipher equivalents may now more readily assume the form of words or phrases.
In any event there will remain the demonstrable kinship between the musical and the cryptographic mind. The ready assimilation of music to symbolic communications systems and language structures; the consensus that music has an import related to its own structure; the prevalent feeling that music is itself a mysterious language intelligible only to the initiated: all these and other affinities and analogies between music and cryptography at least suggest that the relation is not without psychological or aesthetic significance.
Grove5 (T. Dart)
WolfH, ii, 464ff
G. Porta: De furtivis literarum notis (Naples, 1563, 3/1602)
E. Tabourot: Les bigarrures du Seigneur des Accords (Rouen, 1584/R)
D. Schwenter: Steganalogia et steganographia (Nuremberg, c1620)
F. Godwin: The Man in the Moone, or A Discourse of a Voyage Thither (London, 1638)
J. Wilkins: Mercury, or The Secret and Swift Messenger (London, 1641)
A. Kircher: Musurgia universalis (Rome, 1650)
G. Schott: Schola steganographia (Nuremberg, 1655)
J. Friderici: Cryptographia (Hamburg, 1685)
E. Guyot: Nouvelles récréations physiques et mathématiques (Paris, 1769–70)
P. Thicknesse: A Treatise of the Art of Decyphering, and of Writing in Cypher (London, 1772)
W. Hooper: Rational Recreations (London, 1774)
J. Klüber: Kryptographik (Tübingen, 1809)
A. Bertini: Stigmatographie, ou L’art d’écrire avec des points (Paris, 1811)
‘Cipher’, Rees’s Cyclopaedia (London, 1819–20)
F. Sudre: Langue musicale universelle (Paris, 1866)
J. Schooling: ‘Secrets in Cipher I–IV’, Pall Mall Magazine, viii (1896), 119–29, 245–56, 452–62, 608–18
L. Couturat and L. Leau: Histoire de la langue universelle (Paris, 1903)
A. Meister: Die Geheimschrift im Dienste der päpstlichen Kurie (Paderborn, 1906)
J. Devos: Les chiffres de Philippe II, 1555–1598 (Brussels, 1950)
‘Codes are Fragile’, Spring 3100, xxiii (New York, 1952), 10–13
B. Bischoff: ‘Übersicht über die nicht diplomatischen Geheimschriften des Mittelalters’, Mitteilungen des Instituts für österreichische Geschichtsforschung, lxii (1954), 1–27, esp. 6, 18–19
N. Cazden: ‘Staff Notation as a Non-Musical Communication Code’, JMT, v (1961), 113–28; [see also idem: ‘Forum’, ibid., 287–96
D. Kahn: The Codebreakers (New York, 1967)
H. Davies: ‘The History of a Cipher’, ML, xcviii (1967), 325–9
O. Wessely: Musik (Darmstadt, 1973), 226–46
G. Otter and F. Schinn: Biographische Skizze von Michael Haydn (Salzburg, 1808)
L. Spohr: Selbstbiographie (Kassel, 1860–61)
G. Auric: ‘Gabriel Fauré’, ReM, vi/2 (1924), 100–03
P. Dukas: ‘Adieu à Gabriel Fauré’, ibid., 97–9
ReM, x/7 (1929) [Roussel issue]
A. Capri: Giuseppe Tartini (Milan, 1945)
K. Geiringer: Symbolism in the Music of Bach (Washington DC, 1956); repr. in Lectures on the History and Art of Music (New York, 1968), 123–37
J. Krause: ‘Gestalten und Zahlen im “Et incarnatus est” der h-moll-Messe Bachs’, Saarbrücker Hefte, xix (1964), 1–16
E. Sams: ‘Did Schumann use Ciphers?’, MT, cvi (1965), 584–91
E. Sams: ‘The Schumann Ciphers’, MT, cvii (1966), 392–400
E. Sams: ‘The Schumann Ciphers: a Coda’, ibid., 1050–51
E. Sams: ‘Politics, Literature and People in Schumann’s op.136’, MT, cix (1968), 25–7
E. Sams: The Songs of Robert Schumann (London, 1969, 3/1993), 22–6
B. Large: Smetana (London, 1970)
E. Sams: ‘Elgar’s Cipher Letter to Dorabella’, MT, cxi (1970), 151–4
E. Sams: ‘Elgar’s Enigmas’, ibid., 692–4
E. Sams: ‘A Schumann Primer’, ibid., 1096–7
E. Sams: ‘Variations on an Original Theme (Enigma)’, ibid., 258–62
E. Sams: ‘Brahms and his Clara-Themes’, MT, cxii (1971), 432–4
E. Sams: ‘Brahms and his Musical Love-Letters’, ibid., 329–30
H. Halbreich: ‘Ciphered Creed’, Music and Musicians, xx/12 (1971–2), 18–19
D. Brown: ‘A Note on Désirée Artôt, “Fatum”, and the First Piano Concerto’, Tchaikovsky: a Biographical and Critical Study, i (London, 1978), 197–200
Code and Cipher: the Secret Language of Music, Central Television film (1989)
H. Noguchi: ‘Mozart: Musical Game in C K. 516f’, MISM, xxxviii (1990), 89–102
R. Tatlow: Bach and the Riddle of the Number Alphabet (Cambridge, 1991)
S. Bruhn, ed.: Encrypted Messages in Alban Berg’s Music (New York, 1998)
E. Sams: ‘Elgar’s Enigmas’, ML, lxxviii (1998), 410–15
E. Sams: The Songs of Johannes Brahms (forthcoming)